Insight Blog
Agility’s perspectives on transforming the employee's experience throughout remote transformation using connected enterprise tools.
20 minutes reading time
(4012 words)
What is QR Phishing? The Secret Way Cybercriminals Use Quishing Phishing to Steal Your Data
Learn how cybercriminals use QR codes in quishing phishing attacks and discover simple ways to spot, avoid, and prevent dangerous QR code scams.
Ever scanned a QR code to grab a menu, join a Wi-Fi network, or make a quick payment?
You might want to think twice before doing it again.
Cybercriminals are turning QR codes into phishing weapons — a rising threat known as quishing.
In fact, according to a 2024 Statista report, over 40% of mobile phishing attacks now involve QR codes cleverly designed to trick users into revealing sensitive data or downloading QR code malware.
These scams — also called QR phishing — work by hiding malicious links behind what looks like a harmless code on a flyer, receipt, or even a restaurant table tent. Once scanned, you're sent to a fake login page where your credentials are stolen in seconds.
The scary part?
These QR code scams are nearly impossible to spot with the naked eye.
As people rely more on contactless tech, quishing phishing is quietly becoming one of the easiest ways for hackers to launch social engineering attacks via QR codes.
Don't worry though — in this post, we'll break down how these scams work, why they're so effective, and how you can stay safe the next time you're tempted to scan, so let start off with What is quishing?
Read this article:
The Role Of Penetration Testing In Cybersecurity Strategy
The Role Of Penetration Testing In Cybersecurity Strategy
The Rising Challenges and Impacts of Cybercrime, Phishing and Quishing
Cyber-crime is no longer a fringe risk; it's a full-blown business model for malicious actors and one of the biggest threats workplaces face in 2025. Globally, cybercrime is projected to cost $10.5 trillion annually by 2025, up from about $3 trillion in 2015.
Phishing — the broader category under which QR-code attacks fall — remains one of the most common initial attack vectors.
For organisations, the numbers are eye-opening: the average cost of a data breach tied to phishing has reached around $4.88 million globally.
Even for smaller businesses, a cyber incident can be terminal: one report puts the median cost of a cyber attack for a small business at about $46,000, enough to force many to shut down.
So what's driving this trend — and where does quishing (QR-code phishing) come in?
Technology shift + user behaviour = opportunity.
Impact: why quishing is such a problem.
Broader business and organisational consequences.
- Security leaders report that for phishing attacks: lost/stolen data happens in ~60%, compromised credentials in ~50%, and ransomware via phishing in ~45%.
- For small businesses especially, cyber incidents are high risk: about 61% of small businesses report some kind of cyber-attack.
- Organisations slow to detect and contain breaches pay significantly more: for example, one statistic holds that breaches discovered later cost about $1.2 million more.
The challenge is multi-dimensional — attackers have scalable, low-cost tools (QR codes, phishing kits, social engineering), organisations are increasingly exposed (remote/hybrid work, unfamiliar devices, fast QR adoption), and the financial stakes are enormous.
Quishing is a key emerging threat in this landscape. 5 Must-Have Cyber Security Control Measures for Small Businesses
What Is Quishing?
Over the past few years, QR codes have become part of our everyday routine — from scanning menus at cafés and checking in at events to making instant payments or accessing Wi-Fi networks without typing a password.
They've made life easier for both users and businesses, creating seamless touchpoints in a contactless world. But as with any technology that gains mass adoption, there's a darker side that's quickly emerging.
Take, for example, a 2024 marketing campaign by a popular fintech startup that featured a floating QR code on TV screens and digital billboards, encouraging people to scan it for a "mystery crypto reward."
Within hours, thousands of people had scanned the code — but soon after, cybersecurity researchers warned that attackers were using near-identical fake ads to redirect victims to phishing sites, stealing login details and crypto wallets.
Around the same time, reports of QR-based scams surged by nearly 27%, according to a cybersecurity trends report from TrendGuard Labs.
This new type of attack is known as quishing, a blend of "QR" and "phishing." It's where cybercriminals embed malicious links into QR codes, tricking users into scanning them with their smartphones and unknowingly giving away sensitive information.
And as QR codes continue to power payments, marketing, and even authentication systems, quishing phishing is expected to become one of the most common tools in the cybercriminal playbook.
To really grasp how dangerous this threat can be, it helps to understand the mechanics behind its two main ingredients — QR codes and phishing — and how together they form a perfect trap for today's connected world.
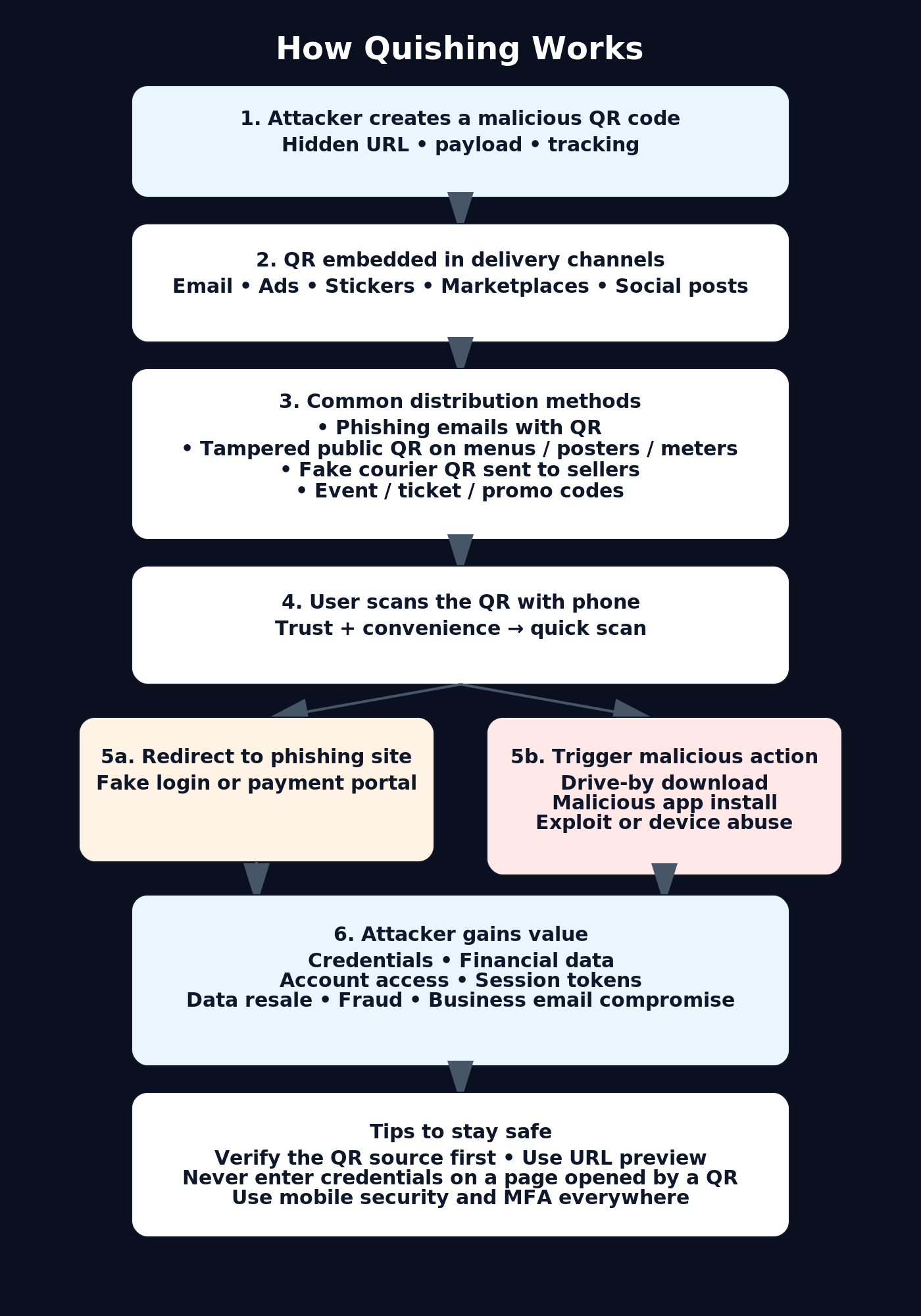
How Does Quishing Work?
Here's how it usually goes.
Cybercriminals create malicious QR codes that look completely harmless — maybe printed on a flyer, included in an email, or even displayed on social media.
These codes can hide links to fake login pages, infected documents, or virus-filled apps. Once scanned, the victim is taken straight to a phishing site that steals their credentials or triggers an automatic download of malware or spyware.
Because QR codes are just images, traditional email filters can't detect the threat. That's why attackers love using them — the code can slip right through spam protection and look like a normal part of an email, poster, or invoice.
In some cases, they even replace legitimate QR codes at cafés, parking meters, or event check-ins with their own stickers to trap unsuspecting users.
A recent rise in QR code scams on online marketplaces shows just how creative these attacks have become.
For instance, scammers posing as buyers have began sending fake courier QR codes to sellers, claiming they're needed to confirm payment or shipping. Once scanned, the link redirects to a spoofed courier website asking for banking details — and just like that, the victim's account is compromised.
This kind of quishing phishing relies on two things most people don't question: convenience and trust. We scan codes without thinking twice, assuming they'll make life easier.
But that quick scan can be all it takes for cybercriminals to access your private information or infect your device with hidden malware.
The best defense? Stay skeptical of any QR code that appears unexpectedly — especially in emails, messages, or unfamiliar public places.
The Most Common Quishing Techniques
Quishing attacks take on many forms, depending on what cybercriminals are after — login credentials, banking information, or access to your device.
While the tactics vary, a few quishing phishing scams have become especially common and worth watching out for:
- Email phishing with hidden QR codes - Instead of showing a suspicious link, attackers now embed a malicious QR code inside emails. When scanned, it takes the victim to a fake login or payment page that looks perfectly legitimate but is designed to steal credentials or financial details.
- QR code sticker swaps - Fraudsters often print their own QR codes and stick them over real ones in public places — like restaurant menus, parking meters, posters, or ATMs. One quick scan can lead you to a cloned website, a malware download, or even a fake app store page.
- Marketplace delivery scams - In early 2025, scammers posing as buyers on Facebook Marketplace began sending fake delivery QR codes claiming they were from well-known couriers such as Australia Post or Royal Mail. The message often says the code is needed to confirm payment or arrange shipping. Once scanned, sellers are redirected to spoofed courier pages that ask for bank details to "receive payment." Similar tactics have been reported across eBay, Vinted, and WhatsApp trade groups.
- Event and ticketing traps - Some fraudsters post QR codes for "exclusive event access" or "free tickets" on social media. These codes usually lead to phishing pages that collect personal data or payment information under the guise of verification.
Staying alert and verifying every code before scanning can help you avoid falling for these increasingly clever scams.
Read this article: : Top 6 AI-Powered Project Management Tools To Use In 2023
Real-Life QR Phishing Scams You Should Know About
Even though quishing phishing sounds like something out of a hacker movie, these scams are happening every day — and they're surprisingly easy to fall for.
Cybercriminals use QR codes in clever ways to get people to visit fake websites, share their bank info, or unknowingly download malware.
From fake courier messages to tampered parking meters, these QR code phishing attacks are showing up everywhere — in our inboxes, on posters, and even on trusted apps.
Here are three real-world QR code scams that reveal just how dangerous (and convincing) these attacks can be:
Example 1 — Fake courier QR codes on online marketplaces
Buyers on Facebook Marketplace (and similar sites) have been sending sellers fake courier/"payment" links and QR codes that look like official messages from postal services.
When sellers scan the code (or click the link) they're sent to a spoofed courier page that asks them to "confirm payment" by entering bank details — which are then harvested by scammers. Authorities and the courier itself have issued warnings after a rise in reports.
Takeaway: treat any courier/payment QR code sent via marketplace chat as suspicious — open the courier's official app or website directly instead of scanning or clicking.
One such scam is the use of a QR code in a phishing message. The QR code masks the actual website and forces the victim to visit the phishing page on their mobile device, which likely does not have the same security protections as their company-issued laptop."
By John Wilson (Senior Threat Researcher at Fortra)
Example 2 — Tampered parking / pay-by-app QR codes (UK motorists)
In the UK, scammers have been placing fake QR stickers over legitimate parking or EV-charging QR codes.
Drivers who scan them are redirected to fraudulent payment pages that capture card details or take payment without issuing a valid ticket.
Local councils and motoring organisations warned drivers to check for tampering and to use official parking apps or card machines. This kind of public-space tampering is a textbook QR code scam that preys on convenience.
Takeaway: if a parking QR looks pasted-on, crooked, or different from the usual signage, don't scan — pay by the official app or machine instead.
QR codes have become a target for cybercriminals in a scam known as 'quishing.
By Greg Hancell (Fraud Expert)
Example 3 — "Free drink" survey that installs malware (Singapore)
A widely reported case involved a customer who scanned a QR code on a bubble-tea shop poster promising a free drink for completing a survey.
The QR led to an Android app download that contained malware; attackers used accessibility permissions to take over the phone and later emptied the victim's accounts — a loss in the tens of thousands.
Singapore police and banks repeatedly flagged similar QR-based malware scams as they spiked in the region.
Takeaway: never install apps from links offered by random QR codes — always use official app stores and be wary of requests to enable accessibility or grant broad permissions.
We have observed a recent and rapid increase in QR code abuse… a new form of social engineering attack labelled 'Quishing' (i.e., QR code phishing).
By Darktrace (Cyber Analyst Team)
How to Detect a Quishing Attack
Spotting a quishing phishing attack isn't always easy — and that's exactly why it works so well.
Cybercriminals often turn to QR code phishing when their usual email tricks stop getting results.
Traditional spam filters and malware detectors look for suspicious links or attachments, but malicious QR codes slip through easily because they appear as plain images or are hidden inside harmless-looking documents.
That means a QR code scam email can land straight in your inbox without raising any red flags.
What makes QR codes especially dangerous is their mystery factor — you can't tell where they lead until you scan them. Scammers use this curiosity to their advantage, pairing it with emotional triggers like fear or urgency to get people to act fast.
A typical example might be a fake notice claiming an overdue bill or parking fine that needs immediate payment. In the rush to "fix" the problem, victims scan the code without thinking, only to be redirected to fraudulent websites or malware downloads.
The bottom line: if an email or message pressures you to scan a QR code quickly, stop and verify it first. That extra moment of caution could save you from a costly QR code phishing attack.
How to Recognize and Avoid a Quishing Attack
Knowing how to recognize a quishing attack can make all the difference between staying safe and becoming the next victim of a QR code scam.
The good news?
Once you understand the red flags, you'll start noticing them everywhere.
Here are some of the most common warning signs to watch out for:
- Unsolicited messages with QR codes: Be cautious of unexpected emails, texts, or DMs asking you to scan a QR code — especially if they claim to be from banks, delivery companies, or government agencies.
- Sense of urgency or fear: If the message says things like "Your account will be locked" or "You must confirm payment now," it's likely a quishing phishing attempt designed to make you act without thinking.
- Generic or suspicious sender addresses: Even if the message looks official, double-check the sender's domain and any mismatched branding before scanning.
- Unfamiliar file attachments: Malicious QR codes are often hidden inside PDF invoices, shipping receipts, or payment confirmations — all made to look genuine.
- Too-good-to-be-true offers: Free gifts, discounts, or rewards via QR codes are classic QR code phishing tactics used to lure people into visiting fraudulent websites.
- Physical QR code tampering: Watch for stickers placed over printed codes in public — especially on parking meters, restaurant menus, or posters. If it looks off-center or mismatched, don't scan it.
- No visible link preview: Before scanning, use your phone's security settings or a QR scanner app with link preview to check where the code leads before opening it.
Always go directly to the source.
If you get a QR code from what looks like your bank or courier, open the official website or app manually instead of scanning the code in the message.
Proven Ways to Protect Yourself Against Quishing Attacks
Staying safe from quishing phishing attacks is all about slowing down, thinking before you scan, and using the same healthy skepticism you would with any suspicious email or link.
While QR code phishing borrows many tactics from traditional phishing, it also introduces a few sneaky tricks that catch people off guard.
Here's how to keep yourself protected, step by step:
1. Verify the Source Before You Scan
Always start with a quick "gut check." Ask yourself — Do I know where this QR code came from?
- Never scan codes from unknown or random sources, especially if they're offering huge discounts, prizes, or "exclusive" deals.
- If the message looks like it came from your bank, delivery service, or HR department, don't scan the QR code immediately.
- Instead, contact the sender through official channels or visit their verified website manually.
- If it's a coworker or client, confirm via chat or call before clicking or scanning anything.
Why it matters: Scammers rely on urgency and convenience. Taking 10 seconds to verify the source can block 90% of QR code phishing attacks before they start.
2. Use Trusted QR Code Scanners Only
Your phone's built-in QR scanner (via Camera, Google Lens, or Apple's native QR reader) is much safer than random apps.
- If you do download a third-party scanner, stick to apps with strong reviews and a large user base.
- Avoid "new" or "free premium" QR readers — cybercriminals have disguised malware as scanner updates to compromise devices in the past.
Pro tip: A good QR app should allow you to preview the link before opening it — this simple feature can save you from visiting a malicious site.
3. Always Preview the Destination URL
Before you tap "Open," check the actual URL that appears after scanning:
- Look for subtle misspellings, odd domain endings (.co instead of .com), or extra words like "secure-login."
- If the link redirects automatically, close the tab immediately.
- When in doubt, type the legitimate website's address directly into your browser instead of following the QR link.
Why it matters: Some malicious QR codes start a silent malware download the moment you access the link. A 2-second check can stop that cold.
4. Be Selective With the Info You Share
If scanning a QR takes you to a login or payment page, slow down.
- Always check the full URL at the top of the page.
- Watch for small inconsistencies — an outdated logo, a missing HTTPS padlock, or slightly off-brand colors.
- Never share passwords, credit card numbers, or bank details via a page you reached through a QR code.
Extra step: Use a password manager — it won't autofill on fake domains, helping you spot phishing instantly.
5. Enable Two-Factor Authentication (2FA)
Even if your login credentials are stolen, 2FA makes it significantly harder for attackers to break in.
- Set up 2FA for your most sensitive accounts (email, banking, work apps).
- Use an authenticator app rather than SMS codes, which can be intercepted.
- If you ever start receiving multiple 2FA prompts you didn't initiate, deny them all immediately — it's a clear sign someone is trying to access your account using stolen info.
Why it matters: In many cases, 2FA alone has prevented quishing phishing victims from losing money or data.
6. Stay Cyber-Aware and Keep Learning
Cybercriminals evolve fast — so should you.
- Take part in security awareness training or free online phishing simulations.
- Follow reliable cybersecurity blogs or your company's IT updates to stay informed about the latest QR code scams.
- Encourage your team to report suspicious QR codes or phishing attempts immediately.
Remember: The more people recognize the signs, the harder it becomes for attackers to succeed.
Treat every QR code like a potential risk until proven safe.
It only takes a few seconds to double-check — but it could save you hours of stress, lost data, or worse, financial loss.
Protect Your Team from Quishing Attacks with AgilityPortal
Don't let a single scan put your company at risk.
AgilityPortal keeps your employees safe with built-in secure communication tools, verified document sharing, and advanced link protection that stops quishing phishing attacks before they spread.
Empower your teams with a centralized, secure intranet where files, announcements, and QR-based resources are monitored and trusted — not random or risky.
✅ Stay connected.
✅ Stay secure.
✅ Stay ahead of cyber threats.
👉 Try AgilityPortal free for 14 days — no credit card needed, just safer communication for your entire organization
Wrapping up
At its core, quishing is a reminder that even the most ordinary technologies can become powerful tools in the hands of cybercriminals.
What started as a simple way to access a menu or make a quick payment has turned into a new frontier for QR code phishing attacks — proof that convenience can sometimes come with hidden risks.
As QR codes continue to appear everywhere — on posters, receipts, social media, and even in workplace emails — users must remember how easy it is for attackers to spoof them.
Scammers rely on curiosity and habit, knowing most people scan without thinking twice. That's why understanding quishing meaning and the ways these attacks work isn't just technical knowledge — it's everyday digital survival.
When it comes to how to prevent quishing, awareness really is your strongest defense.
Taking just a few extra seconds to:
- verify the source of a QR code,
- preview the link before opening it, and
- confirm its legitimacy through an official website or app,
can save you from malware, data theft, and financial loss.
So, why should you avoid scanning random QR codes? Because not every code is what it seems. Some are traps designed to trick your device, steal your details, or drain your accounts.
In the end, staying safe isn't about avoiding technology — it's about using it wisely.
Awareness is the strongest defense, and a quick moment of caution can make all the difference between a normal day and a cyber disaster.
Frequently Asked Questions About Quishing and QR Code Phishing Attacks
Why are phishing attacks so effective?
Phishing works so well because it plays on human emotion — fear, urgency, and curiosity.
When people see messages that say things like "your account will be closed" or "you've won a prize," they act quickly without verifying the source.
Cybercriminals also design fake websites and emails that look incredibly realistic, tricking even tech-savvy users.
Combine that with the rise of mobile browsing and QR codes, and it's easy to see why phishing attacks remain one of the most successful social engineering tactics in the world.
How does quishing work?
Quishing works by replacing the usual phishing link with a QR code that hides a malicious URL. Attackers create these codes and distribute them through emails, flyers, websites, or even fake courier messages.
When someone scans the code, they're redirected to a spoofed login page or infected download, where their credentials or data are stolen.
The trick is that malicious QR codes look identical to legitimate ones, and traditional spam filters can't detect them — making quishing one of the fastest-growing threats in digital security.
Does quishing affect businesses too?
Absolutely. Quishing phishing attacks can target both individuals and organizations.
For businesses, they pose an even greater risk — especially with remote teams, shared devices, and BYOD (Bring Your Own Device) policies.
A single employee scanning a malicious QR code can expose an entire network, leak sensitive data, or trigger ransomware infections.
That's why cybersecurity awareness and regular employee training are critical parts of every company's digital defense strategy.
How do QR codes work so fast?
QR codes work fast because they store data in a grid pattern that your phone's camera can decode instantly.
Each code contains encoded information — usually a URL or text string — that the scanner converts into readable data in milliseconds.
While this makes them convenient for payments, menus, and logins, it's also what makes them dangerous when misused. Attackers exploit this speed and trust to trick users into scanning without thinking, which is exactly how quishing phishing succeeds.
Categories
Blog
(2698)
Business Management
(331)
Employee Engagement
(213)
Digital Transformation
(182)
Growth
(122)
Intranets
(120)
Remote Work
(61)
Sales
(48)
Collaboration
(41)
Culture
(29)
Project management
(29)
Customer Experience
(26)
Knowledge Management
(21)
Leadership
(20)
Comparisons
(8)
News
(1)
Ready to learn more? 👍
One platform to optimize, manage and track all of your teams. Your new digital workplace is a click away. 🚀
Free for 14 days, no credit card required.